This is a deeper dive into one of our case studies where we helped covert-comm.com build their 2 patent-pending platforms:
StegNet
Covert Comm’s state of the art covert communication platform allows users to send data covertly to anywhere in the world bypassing surveillance and bad actors spying on their communication. With recent threats like quantum computing, encryption is at risk and covert comm technology will conceal data even when encryption fails. StegNet assumes encryption has been broken and adds a layer on top of it to assure maximum level of data security.
StegPro
Leveraging state of the art methods, StegPro hides valuable data inside innocuous looking files. You can hide your most valuable files or messages inside other files like images, pdfs and many more. This technology will assure the secrecy and privacy of your data.
Applied Use Case
In this article we will be more specific on use cases and to have a real-life example and architecture of how data hiding and covert communication can truly plug into an environment and start securing different systems communications. This article will be focused on securing Tokenization Services, Data Vaults, Document Management Systems, Persistence Systems and Data Processing Systems.
Ok, let’s dive into our use case. The following architecture shows a high-level view of a standard environment where we have:
- Data processing systems. This could be an online store for example.
- Data Vaults and DMSs. A good practice is to tokenize PII and PCI data instead of passing them around between systems. The actual card data is only saved in a data vault and all processing systems use a tokenized version of it.
- Communication channels. Which are usually https.
In the previous architecture we can see that with the right technology/skill to break an encryption infrastructure, data is compromised in transit between data processing systems and the data vaults (both directions). Data is also easily compromised on the persistence systems. Again, different encryption attacks can make that happen, quantum computing can definitely make it happen and many other threats like backdoored encryption technologies and appliances.
So, what can Covert Comm do about that?
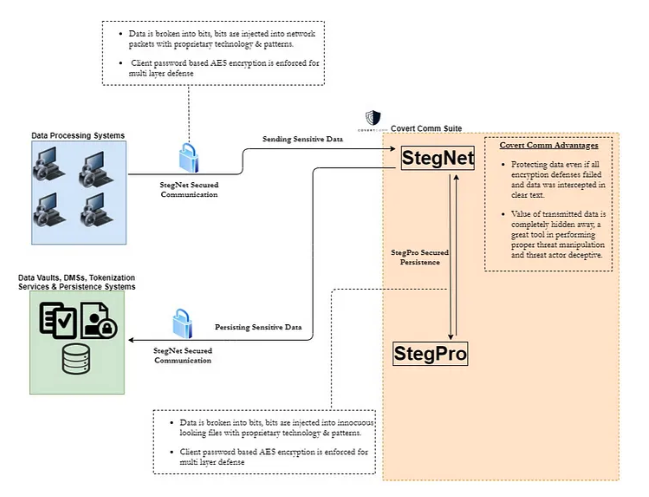
The following diagram shows the same system components. However, this time we are also leveraging data hiding and covert communication to implement layered protection, defense in depth and threat manipulation.
Instead of data processing systems interacting directly with data vaults, covert comm will broker taking care of securing both persistence and communication. Data processing systems will make a call over StegNet secured channels. This means that sensitive data is password based AES encrypted (layer 1 defense) and then broken into bits which are spread across different data packets (layer 2 defense, if someone was to get to your unencrypted data packets and read data in plain text within the body, they still won’t be able to get to your data! Pretty revolutionary!). On the receiving end, StegNet will assemble the data, and pass it on to StegPro. StegPro will password based encrypt and embed the data into a carrier file provided by the user or the calling system (a random pdf invoice or a picture of a puppy, for example). This data will be communicated to the persistence and data vault layers for added security over StegNet.
We say encryption is no longer enough not encryption is bad. So, as you can tell we still use AES encryption but we use it as a second layer of defense not the only layer of defense. Using such technology, in an environment where encryption is partially or completely compromised, data will still be safe both in transit and at rest.
To request the data, the process is very simple. You still use StegNet and StegPro to deliver the data safely out of data vaults and to the calling/processing system. The two platforms can be used directly by users through our user interfaces or command line. Also, they are easily integratable through our fully capable API layer.